#Day6 of #90DaysofDevops challenge
Click here to view the Day6 Task
Create a simple file and do ls -ltr. Change the user permissions of the file and note the changes after ls -ltr
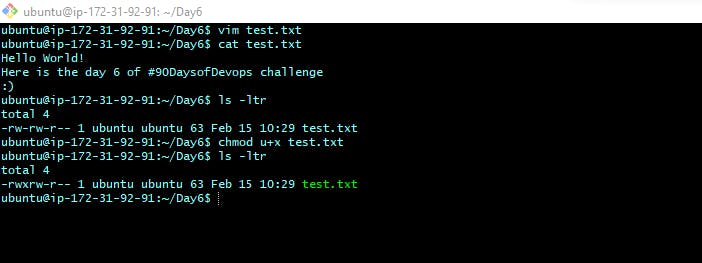
As we can see earlier user permission of 'test.txt' was only read-write. Then changed user permissions to read write execute.
Write an article about file permissions based on your understanding from the notes.
In Linux and other Unix-like operating systems, file permissions are used to control which users and groups can access and modify files and directories.
There are three basic types of permissions that can be set for a file or directory:
Read permission (r): This permission allows a user or group to view the contents of a file or directory. For directories, it also allows the user or group to list the files and subdirectories in the directory.
Write permission (w): This permission allows a user or group to modify the contents of a file or directory. For directories, it also allows the user or group to create, delete, and rename files and subdirectories in the directory.
Execute permission (x): This permission allows a user or group to execute a file (if it is a program or script) or to access a directory and its contents (if it is a directory).
Each file or directory in Linux has three sets of permissions, one for the owner of the file, one for the group that owns the file, and one for all other users. These permissions can be set using numeric or symbolic notation.
Numeric notation uses a three-digit code to represent the permissions for each of the three sets. The first digit represents the permissions for the owner, the second digit represents the permissions for the group, and the third digit represents the permissions for all other users. The values of the digits can range from 0 to 7, with 0 representing no permissions and 7 representing all permissions.
Symbolic notation uses a combination of letters and symbols to represent the permissions. The letters "r", "w", and "x" represent read, write, and execute permissions, respectively. The symbols "+" and "-" are used to add or remove permissions, and the symbol "=" is used to set the permissions to a specific value.
example: For add read write permission to group
#chmod g+rw /test.txt

Read about ACL and try out the commands 'getfacl' and 'setfacl'
Access Control List (ACL) provides an additional, more flexible permission mechanism for file systems.
Access Control List is a service that is in use for providing special permission to specific users and groups for particular directories and files.
Think of a scenario in which a particular user is not a memeber of group created by you but still you want to give some read or write access, how can you do it without making user a member of group, here comes in picture Access Control List, ACL helps us to do this trick.
'getfacl' is used to display the ACL of a file or directory. It shows a list of users and groups that have been granted access to the file or directory, along with the specific permissions that have been granted.

'setfacl' is used to modify the ACL of a file or directory. It can be used to add or remove users and groups from the ACL, and to change the permissions that have been granted.

Both 'getfacl' and 'setfacl' are useful tools for managing file and directory permissions in a more fine-grained way than is possible with traditional Unix permissions. They are often used on systems where multiple users need to share files and directories, or where more complex permission structures are required.
Thank you for reading! 🍁
-Nidhi
